Technical Cyber Security Rating
The Most Comprehensive and Accurate Technical Intelligence.
The Black Kite Technical Rating provides easy-to-understand letter grades and defensible data details behind 20 risk categories. The non-intrusive report passively evaluates third parties, and does not touch an organization’s systems or network assets.
Easy-to-Understand Letter GradesCalculated by Defensible Data
Black Kite follows and applies commonly-used frameworks developed by the MITRE Corporation for scoring software weaknesses in a consistent, flexible, and transparent manner, converting highly technical terms into simple letter grades.
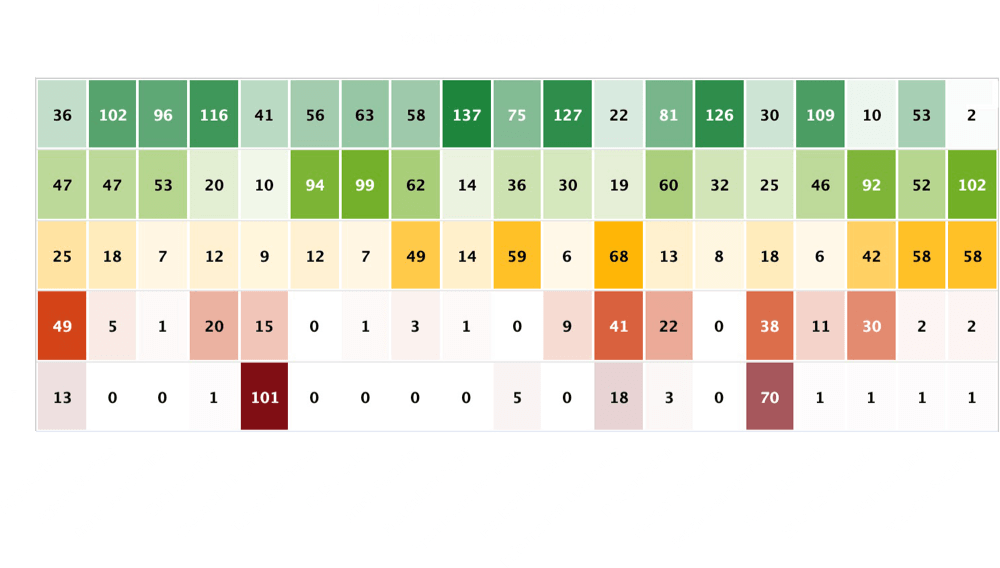
Vulnerability Prioritization
Black Kite provides a graphical distribution in the form of a heat map to determine the status and severity of each finding. Our platform leverages MITRE and NIST to further confirm the criticality of each threat.
Powerful Performance behind 20 Categories
The total score is a weighted average of 20 category components, providing unmatched breadth and insight into detected vulnerabilities.
Tap on items to learn more.

With Financial Impact Correlations

Now That I Have the Data – What Do I Do With It? Black Kite’s Strategy Report
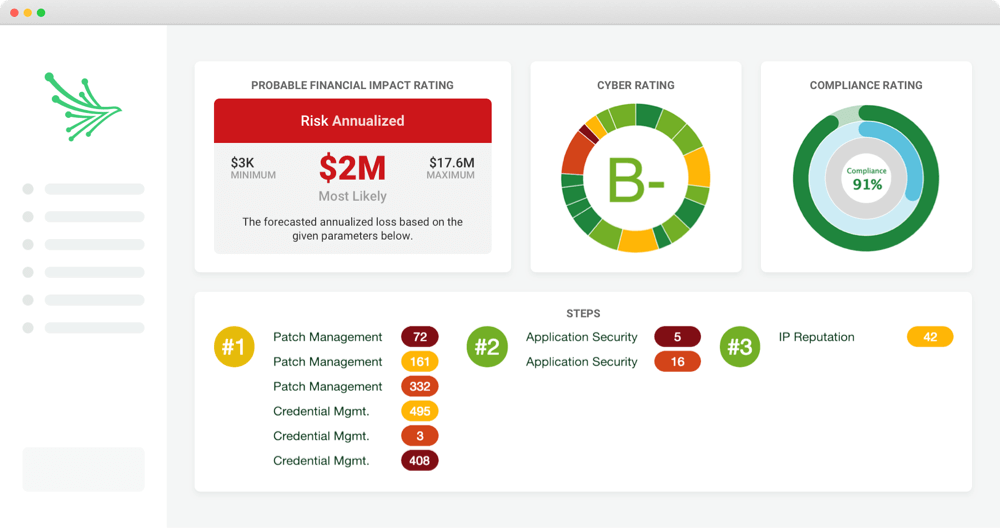
Black Kite’s Strategy Report shares feedback to help executives to understand their cyber risk posture and scale return on cybersecurity investments. The report provides simple steps to help remediate issues and mitigate cyber risks with suppliers and partners. Helpful One-Pager →
Benefits
Receive simple, outlined steps
Multiple formats available for download (PDF, Excel, etc.)
Prioritize tasks based on critically
Trusted by