Reputational Cyber Risk – How to Avoid Business Loss
In the SRS (Security Rating Service) space, why does reputation in cyber security matter?
While the C-suite and boards are aware that reputation loss poses a great threat to business, it is not always on the top of mind from the perspective of the technical team.
In this blog, we define reputational risk, how it is related to cyber risk management efforts, and most importantly – why managing reputational risk matters in the digital era [space].
Understanding Reputational Risk
To be able to understand reputational risk, let’s take a look at the definition.
Reputational risk can be defined as a potential threat or a danger to the good name or standing of a business.
These threats can pose damage to the company’s reputation and eventually affect its revenue. Companies with positive reputations draw in more customers, because they are viewed as trustworthy, having higher value . As a result, their clients are more loyal and often buy more products and services.
One of the greatest risks associated with reputational risk is unpredictability. It can literally come from anywhere, and oftentimes without warning. In cases like these, reputational damage can be devastating to an organization depending on the severity.
It takes many good deeds to build a good reputation, and only one bad one to lose it.
—Benjamin Franklin
The Relation to Business Lost
Reputational risk can pose a danger to the survival of the largest and best-run businesses by wiping out millions or billions of dollars in market capitalization or future profits.
IBM’s recent Cost of a Data Breach Report 2021, summarizing independent research by the Ponemon Institute, [1] addresses the Lost Business cost in a data breach, which is closely related to a reputational loss. According to the this study [1], activities associated with the Lost Business in a data breach mainly includes the:
- Rise in customer turnover
- System downtime resulting in lost revenue
- Effort to obtain new business with the tarnished reputation
Compared to other factors, such as Detection and Escalation, Notification, Ex-post Responde, lost business became the largest contributing cost factor, accounting for nearly 38% of the average total cost of a data breach in the 2021 report.
The Relationship between Risk, Reputation and Data Breaches
Cyber risk is any risk from the digital world, including damage to the reputation of a company from financial loss, operational disruption, and data breach impacts. The cyber risk could emerge in a variety of ways, including:
- Breaches to gain unauthorized access to information systems
- Unintentional or accidental breaches of security
- IT risks due to factors such as poor configuration or poor integrity
While the root-cause of a cyber breach is a larger conversation that needs to be had (check out the 2022 Third Party Breach Report), the resulting reputational damage is undeniable, with a high volume of lost business in many cases.
Take the Target data breach in 2013, which resulted from the criminals gaining access to a third-party vendor in Target’s digital supply chain. The breach window was from November 27 to December 15, 2013 and eventually exposed personal data of 110 million customers.
Target officials discovered the breach within 16 days, and disclosed the news to the public 20 days after discovery. Many blamed Target for the time it took to reveal the incident to the public.
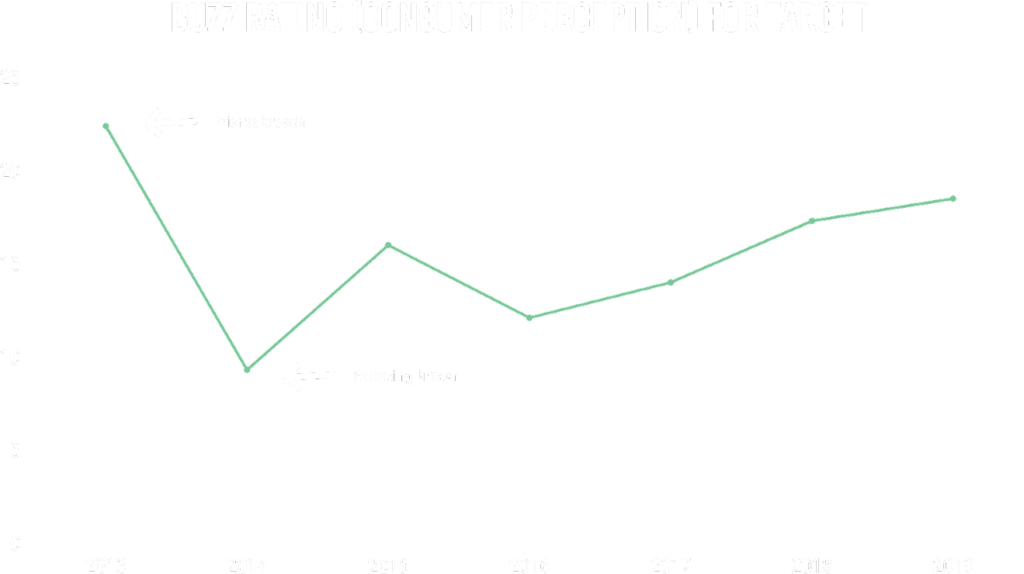
The graph above is based on an ask to respondents by BrandIndex, “If you’ve heard anything about the brand in the last two weeks, through advertising, news or word of mouth, was it positive or negative?” Scores are net scores, calculated by subtracting the percentage of negative responses from the percentage of positive responses for each brand.
After the breach became public, many customers canceled their REDcards and stopped shopping at the retail corporation. As seen in the BrandIndex chart above, the customer perception took a 54.6 percent dip the year following the data breach [2].

Source: Varonis
Target’s breach was one of the biggest data breaches at the time, igniting a conversation about POS protection, customer data security and many other issues often overlooked in the past. Five months after the breach, Target published a list of security [3] measures that included enhanced monitoring and logging, implementation of segmentation, reviewing and limiting vendor access and enhanced security of accounts.
Although Target managed to raise their unfavorable reputation, their 2019 buzz rating is still 18% percent below their 2013 rating.
Another headline breach worth looking at is Uber, in 2016. Uber stands out here because they did not initially report the details of the breach, but instead attempted to cover-up the attack with a payout. By doing this, Uber tarnished their relationship with the customer, losing trust and credibility.
In the initial data breach of 2016, personal information of 57 million Uber users fell into the hands of the attackers, as well as the driver’s license data of 600,000 Uber drivers. However, instead of immediately reporting the breach and alerting those affected, Uber paid the hackers $100,000 to “get rid of the information,” allowing the details to remain hidden until 2017.
Incidents such as this force extreme action and consequences in order to repair relationships and regain trust. The CEO at the time, Travis Kalanick, and Uber’s CSO at the time, Joe Sullivan, both left their roles following the release of the scope of the breach.
California’s attorney general, Xavier Becerra, summarized it well [5], “Uber’s decision to cover up this breach was a blatant violation of the public’s trust.”
To compare to Target, who had a 54.6 percent dip in customer perception the year following their breach, Uber had a massive 141.3 percent dip [2] following disclosure of the breach in 2017.
Reputational Risk as Part of Risk Management
The Target breach is a handy use-case to demonstrate the aftermath of a data breach and how it can affect reputation. It also shows how organizations can fail in managing reputational risk by merely responding to cyber events and hardening breached assets.
Organizations should take a proactive approach in reputational risk management just like they do in vendor risk management. Reputational risk can be quantified and regulated adequately by a company. Such a methodology can help managers better identify current and future risks to the reputations of their businesses, and determine whether to accept a given risk or take steps to avoid or mitigate it.
The Role of SRS in Reputational Risk
In today’s economy, 70% to 80% of the market value comes from intangible assets such as brand equity, intellectual property and goodwill, [4]. This ratio makes businesses extra vulnerable to reputation damaging situations.
With this in mind, Black Kite takes a proactive approach when it comes to reputational risk in the world of cybersecurity by leveraging intelligence when continuously monitoring for risk:
- Brand Monitoring: A business analytics process that monitors various channels on the web or other media to gain insight about the company, brand, or anything explicitly connected to the company
- IP Reputation: Identify if an IP address has a bad reputation or is a member of a botnet.
- Fraudulent Apps: where possible fraudulent mobile or desktop apps on Google Play, App Store and pirate app stores are monitored for hacking or phishing techniques
- Fraudulent Domains: monitor for domain name scams in which unscrupulous domain name registrars attempt to generate revenue by tricking businesses into buying, selling, listing or converting a domain name
- Web Ranking: where the web site of a company is ranked according to popularity, back-links, references, etc.
For each of the above categories, Black Kite assigns a letter grade as well as a rating on a 0-to-100 scale, giving out a measurable indicator of reputational risk. With Black Kite continuous monitoring, a company can monitor its trending reputational risk based on its internet-facing assets, so that risk managers can take proactive actions on their brand reputation.
Learn more about the Black Kite platform and understand how to prioritize managing third party risk.
See the PlatformReferences
[1] Cost of a Data Breach 2021, https://www.ibm.com/security/data-breach
[2] https://www.varonis.com/blog/company-reputation-after-a-data-breach/
[3] https://corporate.target.com/article/2014/04/updates-on-target-s-security-and-technology-enhanc
[4] https://hbr.org/2007/02/reputation-and-its-risks
[5] https://www.npr.org/2018/09/27/652119109/uber-pays-148-million-over-year-long-cover-up-of-data-breach